joy 500
We have the photo and need to find a house address where this photo was made.
We have the photo and need to find a house address where this photo was made.
The task was to reverse file main. This is an executable for MS DOS.
Fortunately, this binary isn't packed and it's logic can be easily understand without dynamic analysis. After few minutes of analysis is becames obvius that this executable set hook for interupt int9 (keyboard handler) and for every input character makes some changes with global variable byte_178. If this variables equals 0x14 then we get success message.
First of all let's take a look at the begging of main function:
The task was to find MD5 of the biggets file from the file HARM.DAT, which is the part of game Harm0597 for MS DOS.
First of all let's ask Google to find this game and easily find URL to download it: ftp://78.46.52.48/pub/mags/harm/harm0597.zip
File HARM.DAT has an obvious structure:
This task is the most simple stego task in this ctf. We have the GIF with 8 frames, all of them have little color difference in the first 3 lines. All we need just to build differences image. After some analysis we decided that it is binary encoded ASCII text. And we decoded it.
As we can see from the task, the talk is about DNA replication, as said my friends from team, we should find the most popular string in the given file.
First of all, I should say, that I'm using python. In the start I just tried to build index where keys are string that can be found in file and values are there frequency. But that didn't work. Because in python index always saved in the RAM, and for my counting, I should have more than 16GB (I think something like 32 or 64). That numbers is reachable, but I guessed that it should be better solution.
Here we need to find something hidden on host http://10.100.0.1/ using given openvpn configs and dump.
In reverse category this task was the easiest one, except Harm (reverse 10), of course:)
The task was to reverse x86 PE executable. There was 2 ways to solve this task: the easiest one and little more complicated. But let's start with their commom part.
The file seems to be packed by UPX, so start debugging! After unpacking by upx we can find that OEP is at address 0x6d28, but there is a very strange code:
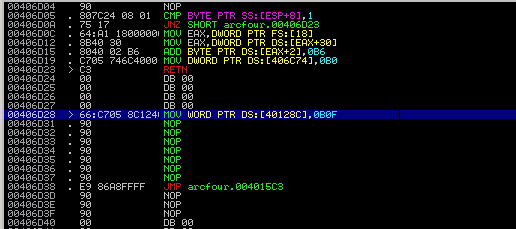
In this task somebody is telegraphing Olimpiada strange messages with secret password and we need to find that.