forensics
cloudfs forensics(200)
We have just finished Ghost in the Shell code CTF in 12th place. Though GITS CTF is usually one of the best CTFs, but this year they weren't that good. The web task had a good idea but wan't correctly implemented, some people got the flag right away from others' exploitations. Forensics tasks wasn't really PURE forensic. Yet, I personally enjoyed the CTF and enjoyed cloudfs challenge.
vodka (forensics 400)
Description: We were given a pcap file called vodka were asked to get out the flag.
Solution:
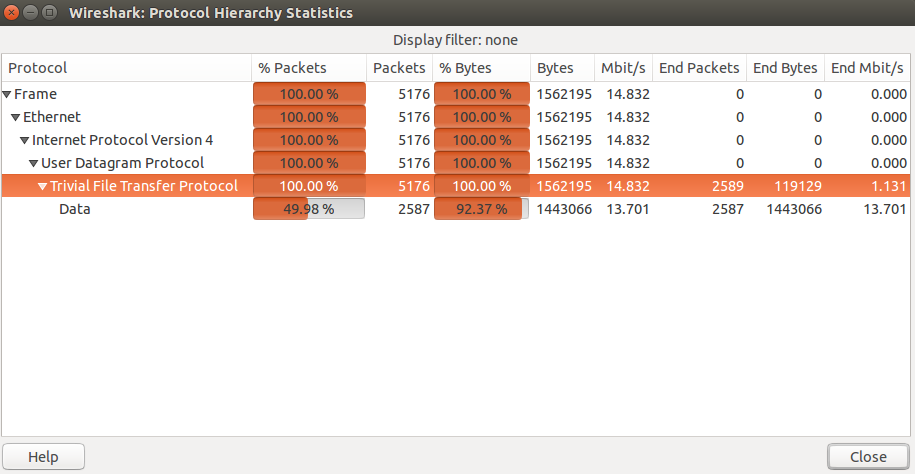
We opened the pcap file with wireshark and take a look the statistics of the pcap file, we saw that 100% of the packets in the file was mainly tftp protocol packets.
Secret host (forensics 100)
Here we need to find something hidden on host http://10.100.0.1/ using given openvpn configs and dump.
NEOQUEST 2014 Quals - Отмороженный компьютер
Дан .vmem дамп памяти, по легенде, полученный с помощью Cold Boot Attack .
Из дампа среди всего прочего можно вытащить .html страницу (руками или через foremost) для ввода кодов деактивации ракет:

По легенде как раз нужно найти "коды отмена пуска ракеты или хотя бы что-то?".
Посмотрим список процессов (например, через фрэймворк volatility):
