WireTap (Stegano 200)
02.11.2014 22:37, by Dor1s
Category:
Event:
Description: Does it sound like a flag? Maybe... I don't know...
File: wiretap.wav
Solution:
Let's quickly analyze the file:
Description: Does it sound like a flag? Maybe... I don't know...
File: wiretap.wav
Solution:
Let's quickly analyze the file:
Description: We were given a pcap file called vodka were asked to get out the flag.
Solution:
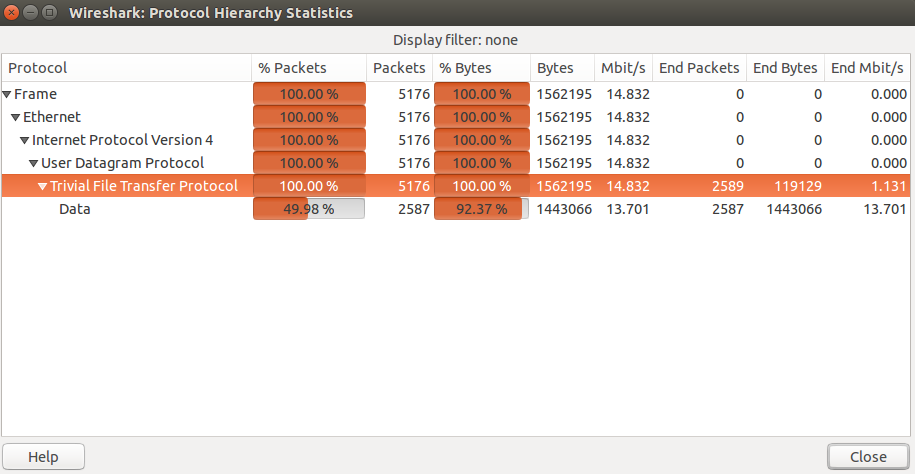
We opened the pcap file with wireshark and take a look the statistics of the pcap file, we saw that 100% of the packets in the file was mainly tftp protocol packets.
Description: Connect to the service listening at 10.210.8.1:6969 and get the flag.
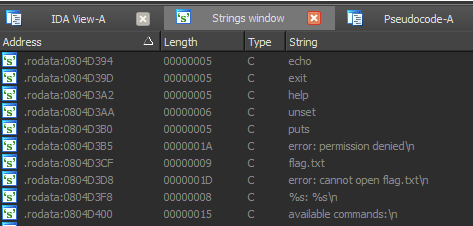
Solution: We have x86 ELF binary (attached to this writeup). If you open it in disassembler, you will find that it's obfuscated, but strings aren't encrypted: