ish (pwn 300)
In this task we have x86 ELF binary ish, which has been run at 54.208.86.14 9988.
This binary is one more Unix shell, but with few commands avaliable:
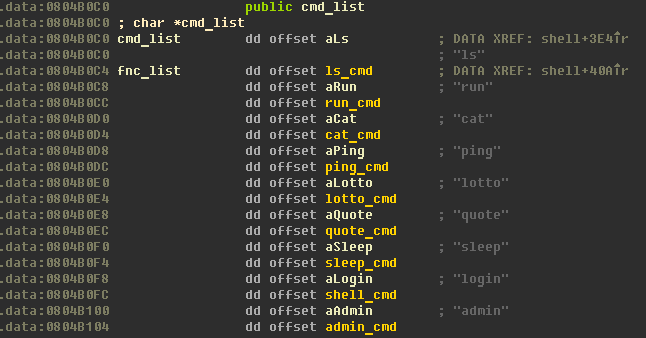
There is only two intresting commands: lotto and login.
lotto
s3 (pwn 300)
Task description gives us only service ip, port (54.165.225.121 and 5333 respectively) and binary, named s3.
Mining Your Rs and Ss (Crypto 500)
[To try to solve the task see an attachment below the writeup]
For this particular task we've been given some sort of CA to issue user certificates and authentication part to verify issued user certificate using SSL handshake. The main purpose according to the message provided after authentication is to login with certificate issued to the user named admin. There is no sense telling that one can not do this in ordinary way by requesting it from CA provided.
AES Broken (300)
This time we are given a rather long file, presumably ciphertext -- the result of AES transformation weak in some sort of way. After taking a look at it in Sublime we can't find anything wrong with it: indeed, Sublime does normally hang after us trying to make a full-text search through the file. Let's better make it binary and open in some lightweight hex editor.
Decrypt the message!
Task:
Decrypt the message!
And 'ecnrypted.txt' is attached to task:
Rolling Hash
Task:
flag="*********"
def RabinKarpRollingHash( str, a, n ):
result = 0
l = len(str)
for i in range(0, l):
result += ord(str[i]) * a ** (l - i - 1) % n
print "result = ", result
RabinKarpRollingHash(flag, 256, 10**30)output is
1317748575983887541099
What is the flag?
Solution:
What is this
This is most common task where we have two images with black and white pixels and need to XOR them pixel by pixel. Let the white pixel be 1 and black pixel be 0. Further description is not needed. Code is attached. Flag is AZADI TOWER.
Hidden message
There we got a dump of UDP packets in pcap file.
xorcise (exploit 500)
We've got the following binary and its source code: xorcise.
$ file xorcise xorcise: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked (uses shared libs), for GNU/Linux 2.6.32, not stripped
Looking attentively at source code you can find this interesting moment in decipher function:
