This time we are given a rather long file, presumably ciphertext -- the result of AES transformation weak in some sort of way. After taking a look at it in Sublime we can't find anything wrong with it: indeed, Sublime does normally hang after us trying to make a full-text search through the file. Let's better make it binary and open in some lightweight hex editor.
cat ciphertext | xxd -r -p - > ciphertext.bin
Well, now by simply looking through the cipher text (so conveniently formatted by hex editor into lines of aes blocksize length), you can easily notice repeating blocks. For normal aes cipher in ecb mode that's not very strange, but let's find out, how much repeats of given cipher text block we have. About a thousand of repeats?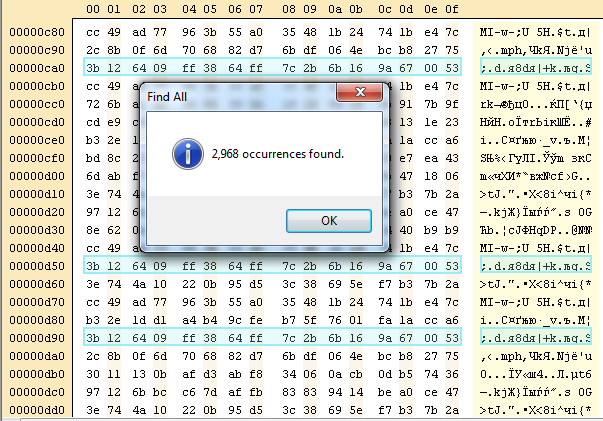
Well, that's strange indeed! Sharif guys, did you encrypt one char of plaintext per block?
Now we use a simple script to count different cipher text blocks in file.
#!/usr/bin/python
from sets import Set
import operator
with open('ciphertext','r') as f:
output = f.read()
uniques=dict([])
for i in xrange(len(output)/32):
word=output[32*i:32*i+32]
if uniques.has_key(word):
uniques[word]+=1
else:
uniques[word]=0
print len(uniques)
print uniques
27 block seem to be covering 26 characters of English alphabet plus the space.
Modify the script to replace blocks by characters:
for (block,c) in zip(uniques,map(chr, list(xrange(ord('A'), ord('Z')+1)) + list([ord(' ')]))):
output=output.replace(block,c)
print outputNow feed the output into cryptool:
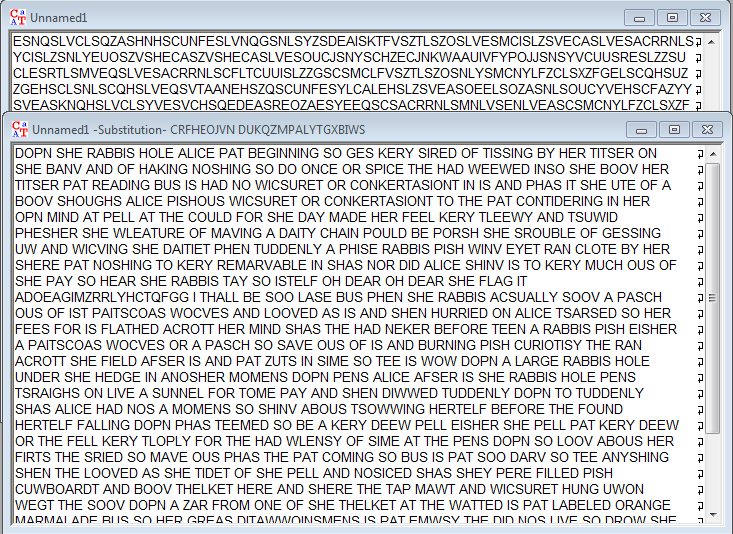
Now correct some badly-guessed permutations over alphabet and get the flag: "flag is adoeagimjrrlyhcsqfgg"
Well, Alice, how many ctfs have you already seen? How many do still await you?
best Running shoes | Nike SB