Description: We were given a pcap file called vodka were asked to get out the flag.
Solution:
We opened the pcap file with wireshark and take a look the statistics of the pcap file, we saw that 100% of the packets in the file was mainly tftp protocol packets.
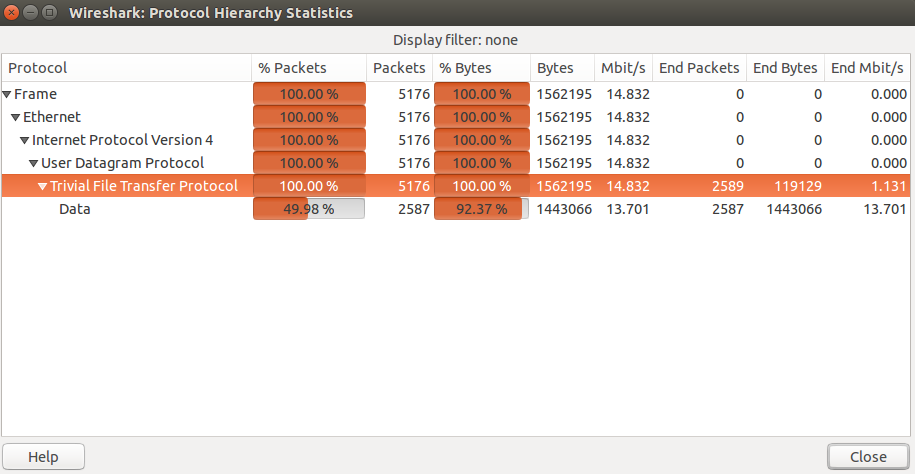
Looking at the first packet in the pcap, we see a write request with a file named "openwrt-wrtsl54gs-squashfs.bin" and then we see the blocks are send with size 558 bytes and after each block we see an acknowledgment of receiving the block.
What we simply need now is to dump that binary file from the pcap. Using this command on tshark:
tshark -r vodka.pcap -Y "tftp and tftp.opcode==3" -Tfields -edata > openwrt-wrtsl54gs-squashfs.hex
The file now is dumped. However, it is in hex not in binary because the output of tshark is in hex. We wrote a simple python code to change the file from hex to binary.
f = open('openwrt-wrtsl54gs-squashfs.hex', 'r')
w = open('openwrt-wrtsl54gs-squashfs.bin', 'wb')
lines = f.readlines()
for l in lines:
w.write(l.strip('\n').decode('hex'))
w.close() Now we have the binary file. The first thing we did is we ran the "file" command trying to now the type of the file, but the output of file was nothing except "data". Then we use "binwalk" and that was the result of binwalk.
DECIMAL HEX DESCRIPTION ------------------------------------------------------------------------------------------------------- 32 0x20 TRX firmware header, little endian, header size: 28 bytes, image size: 1323008 bytes, CRC32: 0x6CAC483 flags/version: 0x10000 60 0x3C gzip compressed data, from Unix, NULL date: Thu Jan 1 02:00:00 1970, max compression 517152 0x7E420 Squashfs filesystem, little endian, version 2.1, size: 805671 bytes, 269 inodes, blocksize: 65536 bytes, created: Wed Oct 29 20:53:25 2014
So, there is a squash file system and there is a firmware. We thought that we will get the squashfs using dd, mount it and then get the flag. We "dded" the binary file and tried to mount the squash file system, but the mount has failed. Probably, to mount the squashfs correctly we need to read the firmware to extract some options and then we should be able to mount the squash fs correctly. We googled a bit about the squash fs and TRX firmware and we found this tool.
We downloaded the tool and compile it. Using "extract-firmware.sh" in the tool with the openwrt-wrtsl54gs-squashfs.bin as input, we managed to mount the squash file system correctly. Browsing the squashfs folder, we found three folders: "image parts", "logs" and "rootfs".
That was the content of the rootfs:
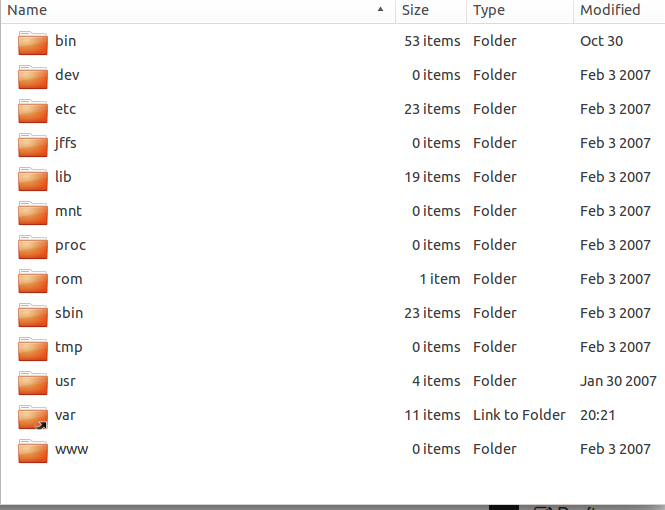
I entered the rootfs and found a minimal linux system. Not sure were to go in this system, I assumed that there will be something inside the "www" folder. I checked it, but it was empty. I decided to grep the entire system for the word "flag". I found a huge output. That was one of the lines in the output of the grep command.
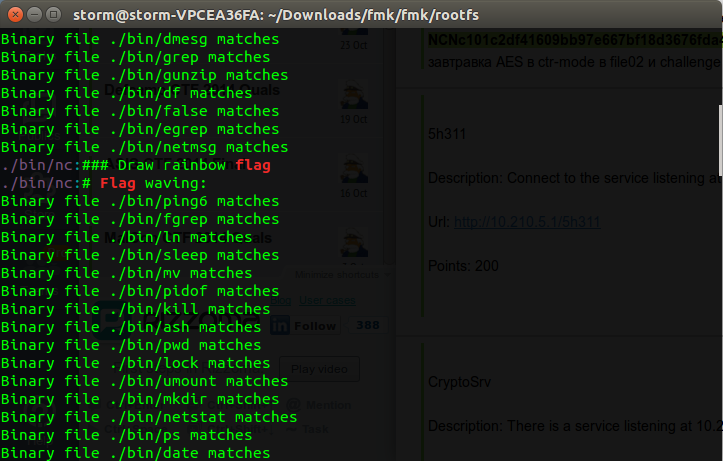
Looks like the nc file is interesting. I checked the file, it was basically a bash file. Checking the source code of the nc file, I found in the comments this section.
###################### ### Draw rainbow flag ######################
I decided to run the nc file after making sure it doesn't have something malicious, and that was the result of running it.

Looking at the bottm right corner of the output we see "NCNdeadface" which was simply the flag.
flag: NCNdeadface
PS: I managed to solve this after the end of the competition with like 15 mins. The reason why, is that the grep on flag returned a huge amount of data.
Running sports | jordan Release Dates