In these tasks we were given a service which:
- accepts .cpp file
- compiles it via MSVS10 or gcc4.8 (you can choose which one)
- launches a couple of tests on successfully compiled binary
You can look at it here, here and here.
Also there are original source code files, which are vulnerable and unstable. Tests launched on the service are checking some vulnerabilities on compiled binaries and our goal is to fix them and prevent program from crashing.
Well, the best way to show how we have solved these tasks is to show diff between original source code files and our solutions. Look at this commit.
When uploaded source code passes all tests and keeps its initial functionality the service prints messages like:
WON!
Flag: b658c70eb17bf96d6f8d64145b4cc859
WON!
Flag: 57ba58587f972a80c12b5f590078270c
WON!
Flag: 696570afe73d9e8cbd206d10dbf58e8b
I don't think that it is needed to describe each line in our solution. But I mention most popular vulnerabilities fixed in these tasks:
- buffer overflow
- writing to unallocated memory / reading uninitialized memory
- format string vulnerabilities
- few other errors
If you would have any questions about our code ask it via our twitter account. We will answer and try to explain our fixes.
Btw, my lovely fix is:
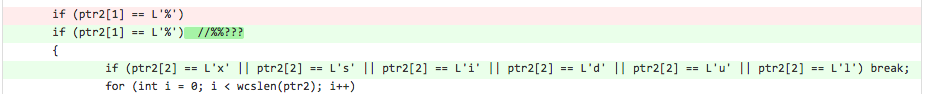
At the end of CTF we had just one vulnerability in our source code and suddenly we understood that input like "%%x" crashes the program. I could not come up with anything better than such fix and we got the 1st place when CTF was 12 minutes left.
p.s.
If service tells you complier error, try to choose another compiler ;)
Adidas shoes | NIKE HOMME