Description:
Download the file and find the flag.
Solution:
After downloading and uncompresing file we can see that it's x64 ELF binary. When I opened it in IDA, I've found that there are tons of code, which seems to be created by flex (The Fast Lexical Analyzer):
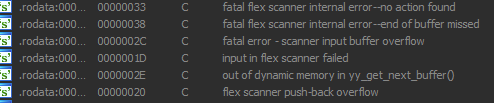
Because I was lazy to analyze this program I desided to make small hack. The flag is a string and it should be returned by program when I enter something. Because this program seems to use "std::operator<<" to ourput everything:
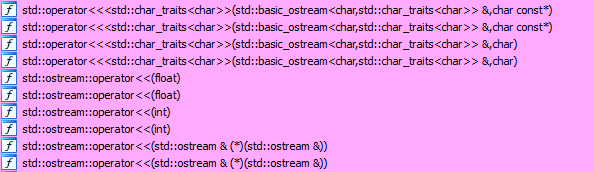
(and strings, in particular), lets find where single char output is used:
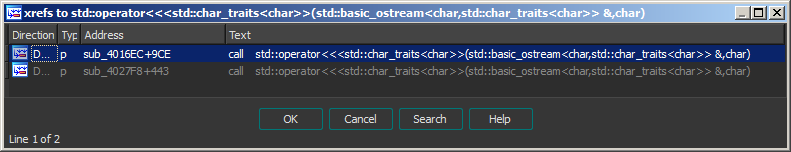
Only 2 functions! Go to first one and find:
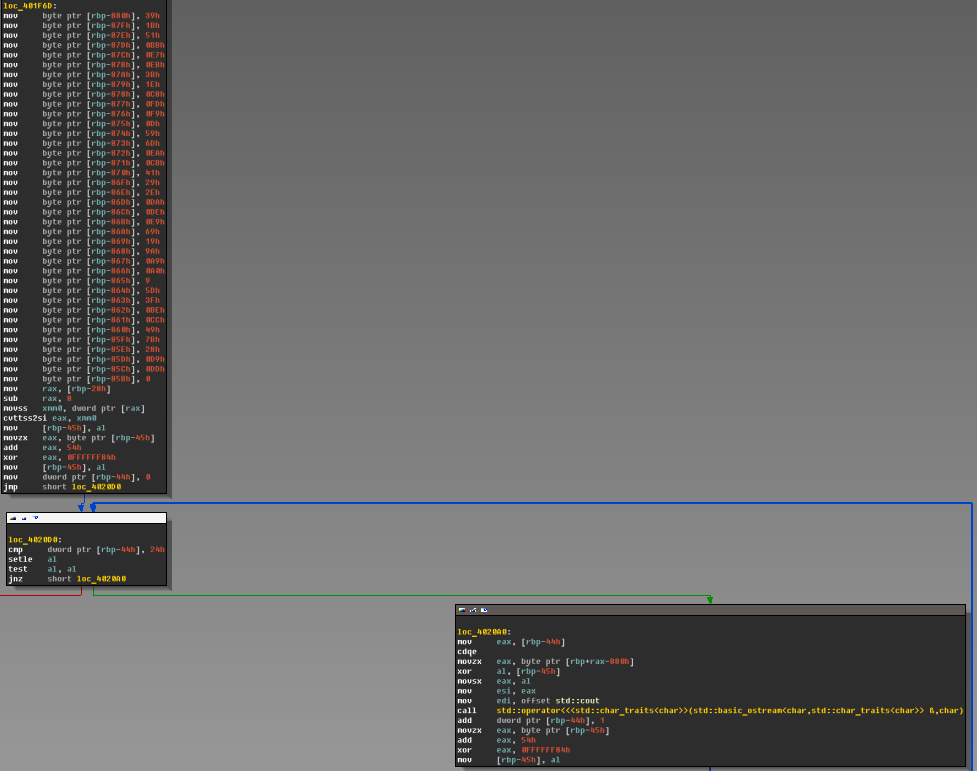
Char array of 37 symbols... maybe it's flag? Lets check.
Decrypt char array routine is the next:
And my decryption code (IDA command line with idapython used):
Python>#get bytes a = [] for i in range(37): a.append(Byte(0x0401F6D+6+i*7)) #brute single byte xor import string for i in range(256): t = i s = '' for el in a: t =((t+0x54)^0x84)&0xff c = chr(el^t) if c not in string.printable: break s += c if len(s)==37 and 'ASIS' in s: print(s) Python> ASIS_cc605aeae2c9a62fa11ba8ae7fd1301e
Too easy! So, the flag is ASIS_cc605aeae2c9a62fa11ba8ae7fd1301e
affiliate tracking url | Best Selling Air Jordan 1 Mid Light Smoke Grey For Sale 554724-092