Task:
Silly Gunslinger Joe has learned from his mistakes with his private terminal and now tries to remember passwords. But he's gotten more paranoid and chose to develope an additional method: protect all his private stuff with a secure locking mechanism that no one would be able to figure out! He's so confident with this new method that he even started using it to protect all his precious gold. So … we better steal all of it!
SSH: joes_gold@wildwildweb.fluxfingers.net
PORT: 1415
PASSWORD: 1gs67uendsx71xmma8
Solution:
Start with ssh connection to the given server (whatever). In the home directory I found two files: FLAG and gold_stash.
joes_gold@goldstash:~$ ls -la total 32 drwxr-xr-x 2 joes_gold joes_gold 4096 Oct 6 23:09 . drwxr-xr-x 3 root root 4096 Oct 6 22:56 .. -rw-r--r-- 1 joes_gold joes_gold 3106 Feb 20 2014 .bashrc -r-------- 1 gold gold 46 Oct 6 23:04 FLAG -rwsr-sr-x 1 gold gold 13186 Oct 6 23:03 gold_stash
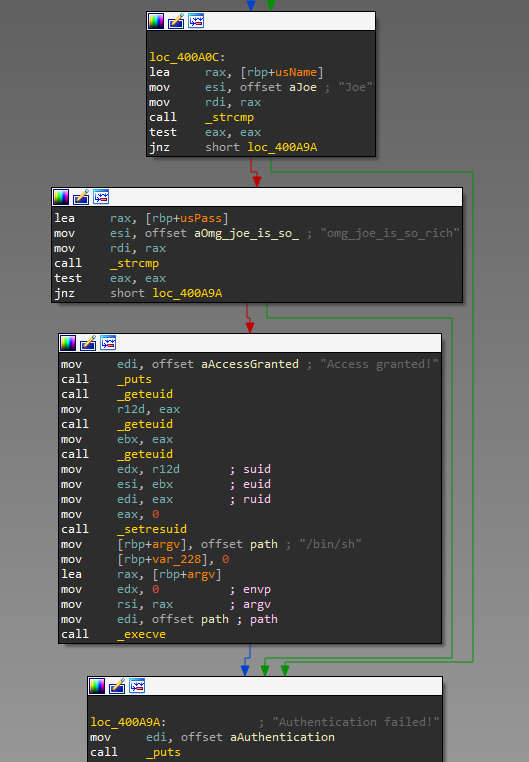
So I didn't have enough rights to read FLAG but I sill could run gold_stash and found the way how it can read FLAG for me. I ran gold_stash and it asked me for username and password to authenticate.
joes_gold@goldstash:~$ ./gold_stash
(_/-------------_______________________)
`| /~~~~~~~~~~\ |
; |--------(-||______________________|
; |--------(-| ____________|
; \__________/'
_/__ ___;
,~~ | __--~~ Gunslinger Joe's
' ~~| ( | Private Stash of Gold
' '~~ `____'
' '
' ` Password Protection activated!
' `
'--------`
Username:
Password:
Authentication failed!I copied it to my desktop and 'strings' gave me: Joe and omg_joe_is_so_rich were found. Back to server.. enter username and password.. fail.. O_o. Ok, then I tried to check password locally.. and it was correct!
It seems to be time to RE.. but:
nothing new...
Ok, back again to server: I copied gold_stash to /tmp and start it.. password was ok, but suid bit was not copied and I was not able to read FLAG. So, something wreck my input or smth else.. I did 'lsmod' and found one strange module 'joe.ko'.
Then I've started RE it. In short this driver hooks sys_read and modify result of sys_read (name it as usInput) if it matches some conditions. The conditions are:
- if (some current_task parameter doesn't match smth) don't change anything;
- if (usInput == "omg_joe_is_so_rich") set usInput to encrypt(usInput);
- if (encrypt(usInput) == "omg_joe_is_so_rich") set usInput to "omg_joe_is_so_rich".
So I should have found such st that match encrypt(st) == "omg_joe_is_so_rich". Encrypt function code is quite simple:
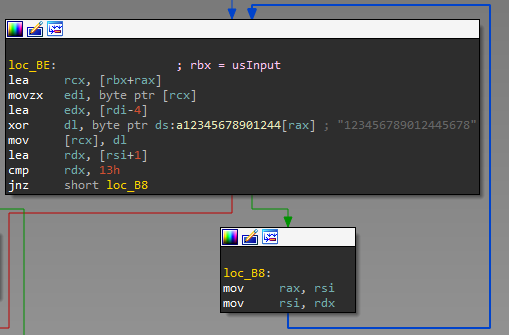
and valid password can be recieved by the following code:
>>> k0 = '123456789012445678' >>> k1 = 'omg_joe_is_so_rich' >>> ''.join([chr((ord(k0[i])^ord(k1[i]))+4) for i in range(len(k0))]) 'bcXoc]VkTGrE_oKcXT'
and now...
joes_gold@goldstash:~$ ./gold_stash
(_/-------------_______________________)
`| /~~~~~~~~~~\ |
; |--------(-||______________________|
; |--------(-| ____________|
; \__________/'
_/__ ___;
,~~ | __--~~ Gunslinger Joe's
' ~~| ( | Private Stash of Gold
' '~~ `____'
' '
' ` Password Protection activated!
' `
'--------`
Username: Joe
Password: bcXoc]VkTGrE_oKcXT
Access granted!
$ cat FLAG
flag{joe_thought_youd_never_find_that_module}The flag is: flag{joe_thought_youd_never_find_that_module}
