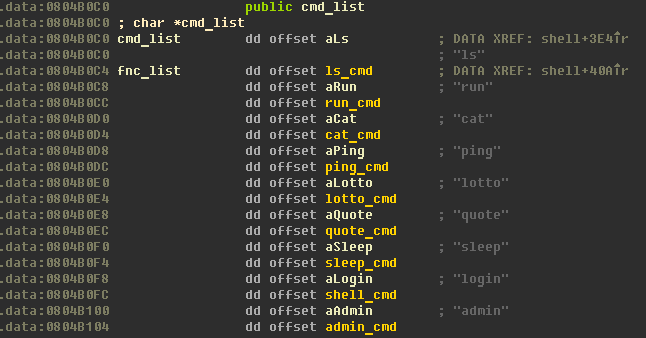
Task:
Lots of criminals in this area work for one big boss, but we have been unable to determine who he is. We know that their organization has one central personnel database that might also contain information about their boss, whose username is simply “boss”. However, when you register in their system, you only get access level zero, which is not enough for reading data about the boss - that guy is level 10. Do you think you can get around their protections?
nc wildwildweb.fluxfingers.net 1410
Note: The users dir will be wiped every 5 minutes
And a .c file attached (attached to write-up below)
Solution: